Exclusive: He was good. Very good, the truth is.
But the Medibank hacker had a weak point: his ego.

“Ermakov had some sloppy tradecraft and at ASD, you can only make that mistake once if you’re a criminal,” ASD Acting Director-General Abi Bradshaw advised 9News in an unique interview.
ASD’s response group, led by senior cyber spy “Joan”, recognized some specific methodologies within the hacker’s assault on Medibank’s networks and knew the place to look to start the hunt.
“Within days of the attack, we had a very strong confidence that he was operating out of Russia,” Joan stated.

The darkish internet is a hangout for cybercriminals promoting all kinds of illicit and harmful items, from firearms to medicine, pornography and stolen knowledge.
And positive sufficient, ASD discovered a few characters purporting to have the leaked Medibank knowledge.
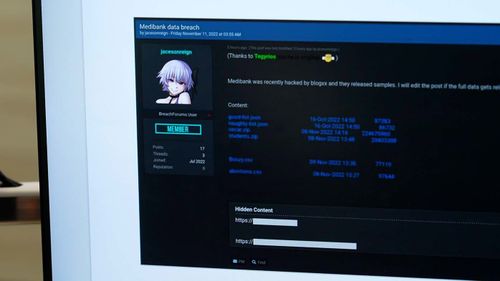
One was known as “Tegyrios”.
The different had the net moniker “Jacenreign”.
On shut inspection, ASD cyber spies, posing as potential patrons, confirmed that Tegyrios and Jacenreign certainly had the Medibank knowledge.
But neither was the unique hacker.

Here is the place Ermakov’s ego tripped him up.
“There is an element of complacency for cybercriminals like Ermakov,” Joan explains.
“They don’t expect to get caught. So for somebody like us, we play on that, which is why we’re able to find them in places that they may not expect us to be looking.
“Forums the place they assume that they’ve appropriately disguised themselves, or on social media the place they assume we will not determine them.”
Joan is ASD’s director of counter-cybercrime.
She has a PhD in criminology and was in charge of a team of forensic experts, psychologists, lawyers and computing experts.
The joint ASD-AFP Medibank investigation involved 90-100, many of whom are used to exploring the dark recesses of the online world.
“There are many spiders at midnight internet and a few of these spiders are ASD spiders, and a part of our job is to hang around in these darkish internet boards,” Bradshaw says.
“To think about the place cyber criminals could also be lurking, to hearken to their conversations, and to obtain data in that approach.”
There were many dead ends in the Medibank investigations, Bradshaw says, but it was Ermakov’s overconfidence that brought him unstuck.
Ermakov was using various aliases in an attempt to disguise his identity.
Jim Jones was one of Ermakov’s online identities.
Others were “gustavador”, “bladerunner” and “iaas_ermak”.
But one thing he couldn’t change was his methods.
And they allowed a triangulation of digital data, aided by the work of the Australian Federal Police and intelligence agencies in the UK and UK, including the FBI and GCHQ.
Various data points allowed ASD to slowly identify Ermakov as the Medibank hacker.

Aiding the cyber spooks was his known association with the Russian ransomware group REvil, which was responsible for various cyberattacks across the globe, including the May 2021 sting on Colonial Pipeline and the cyberattack on software company Kaseya two months later.
JBS Meats in Australia was also affected in 2021 when REvil targeted its US parent company.
Ermakov, a 33-year-old Moscow resident, has been slapped with travel and financial sanctions by Australia but he has not been arrested.
That said, Ermakov’s ability to trade stolen data has been curtailed now his anonymity has been blown.
Bradshaw says ASD’s job tracking down his co-conspirators is not finished.
“Ermakov is just one a part of this investigation and I can guarantee you that the devoted officers of ASD and AFP are persevering with this hunt,” Bradshaw said.
9News asked Joan if Ermakov knew he’d been caught.
“I hope he does,” she stated.
Source: www.9news.com.au




